Webhooks
Security Implementation
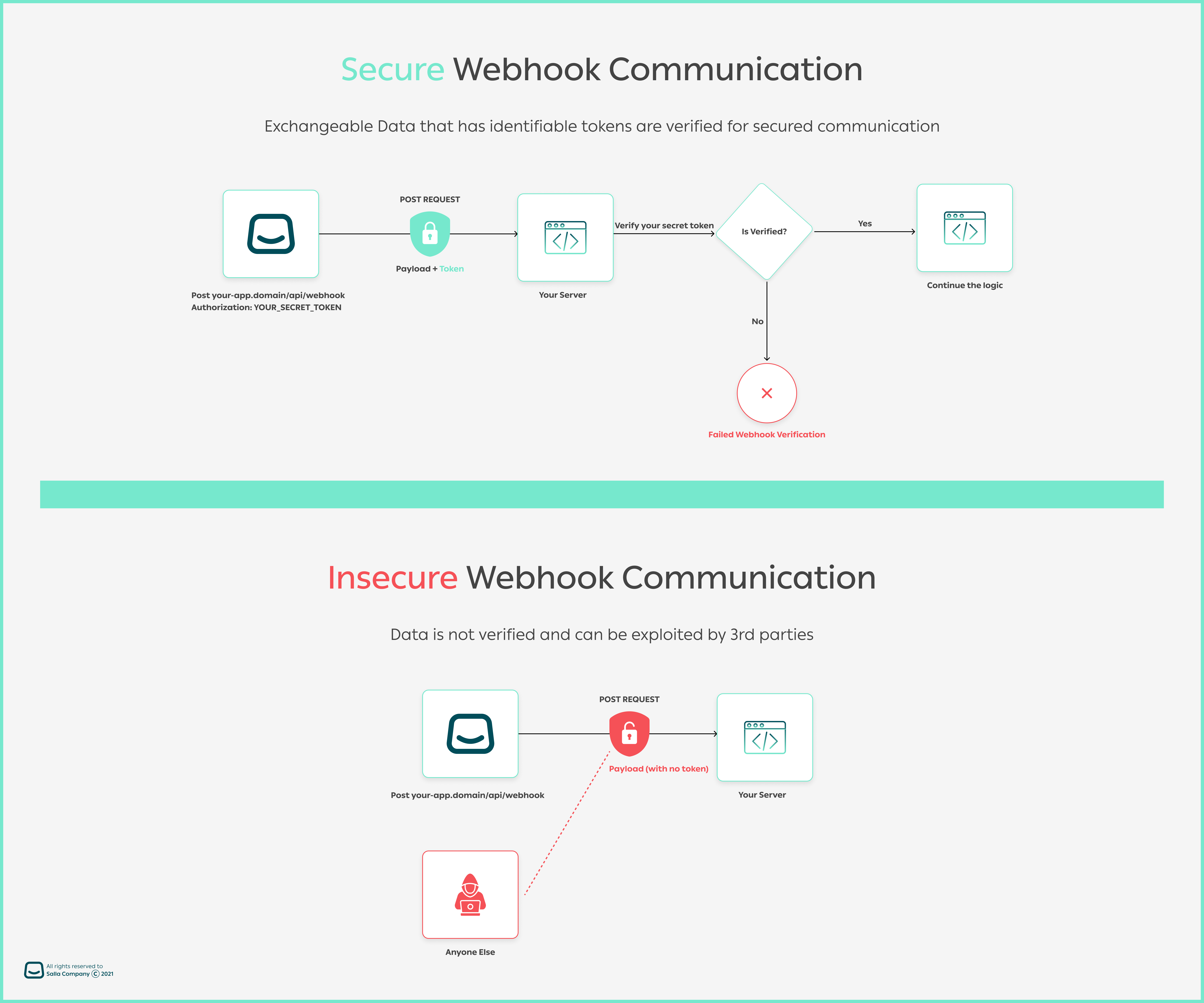
WARNING
POSTing data, allows you to authenticate the sender. Otherwise, deny any other suspicious requests.Regsiter Webhooks
| Parameter | Type | Description |
|---|---|---|
| name | string | Webhook Name |
| event | string | Webhook Event From Event List |
| version | number | Webhook Version; of the webhook; either valued as 1 or 2. |
| rule | string | Operations, expressions and conditions to your webhook. For example, you may use =,!=,AND,OR etc in such a menner: payment_method = YOUR_PAYMENT_METHOD or in combination payment_method = mada OR price < 50. That adds more capbility to filter the response based on conditions |
| url | string | Webhook URL where you will receive the webhook calls |
| headers | array[object] | Webhook headers containing security info |
| headers.key | string | Any haeder key, which its value is sent in the post request to the webhook URL |
| headers.value | string | The value sent to the webhook; for example: cf-ray: 669af54ecf55dfcb-FRA |
| secret | string | Secret Token value |
| version | string | Webhook Version; either valued as 1 or 2. |
| rule | string | Operations, expressions and conditions to your webhook. For example, you may use =,!=,AND,OR etc in such a menner: payment_method = YOUR_PAYMENT_METHOD or in combination payment_method = mada OR price < 50. That adds more capbility to filter the response based on conditions. Read more here |
WARNING
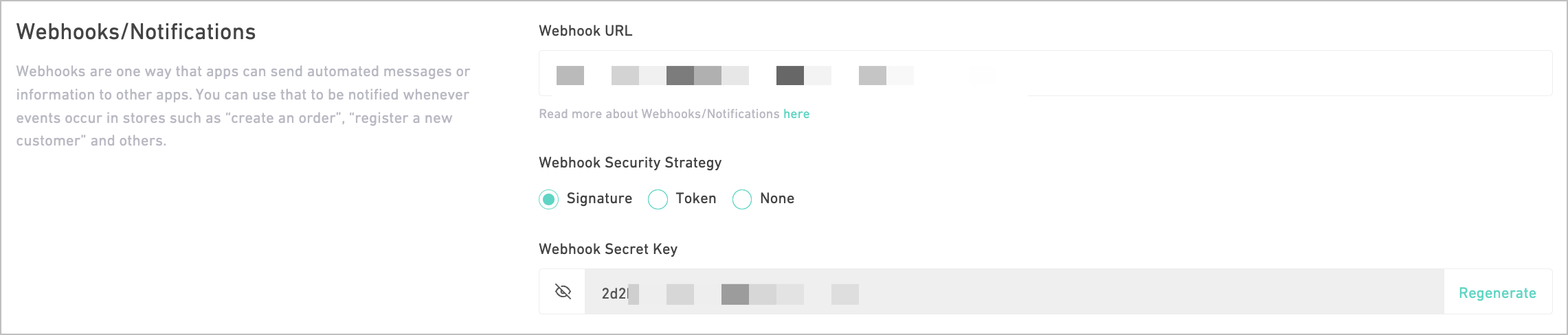
2. By default, all new registered webhooks will be set as version 2. If you want to use version 1 of the webhook, pass that in your request parameter. Additionally, Salla will assign the Security Strategy to Signature by default in case you registered a webhook with no security strategy defined in your body request.Security Strategies
✍️ Using Signature
🔑 Using Token
For all created Partner Apps, Salla will assign the
Following is the expected request payload for the
Once merchants install the app in their stores, Salla uses the Siganture secret startegy (or the default one on app settings) to automatically assign webhook events. A value for Secret must be given when establishing the webhook in order to allow webhook verification. The request body's 64 character SHA256 hash, which you may find via your partner's dashboard, will then be appended to the X-salla-signature header (e.g. x-salla-signature: You can also create your own SHA256 hash of the request body using the Secret value to check the signature. Then, using a timing-safe equality function, compare the header value to your own calculated value. Here is an example of how you might accomplish this using Node.js. Another demonstration can be done using the PHP language to verify a webhook header when receiving a payload. Once the webhook is received, your server can verify it from Salla in the following way:
signature security strategy by default, as Salla will hash payloads via an auto-generated, reproducable signature token. It will also append two headers to the webhook payload; the security startegy used as in X-Salla-Security-Strategy which is in this context Signature , and a hashed token signature as in 4d7dac8e688eca1c1xxxx| Security Startegy | Header | Token Suffix |
|---|---|---|
| Signature | X-Salla-Security-Strategy | X-Salla-Signature |

Register Endpoint
Signature security strategy:webhook_request_body
Verify Webhooks Using Signature
ac3ea83628cccf2e98afc34223e4eeb5b41800b77737938aeed4e109f0a0xxxx).Timeout
CAUTION
List of Salla Store Events
Order
| Name | Description |
|---|---|
order.created | This is triggered when an order has been created. |
order.updated | This is triggered when an order has been updated. |
order.status.updated | This is triggered when an order status has been updated. |
order.cancelled | This is triggered when an order has been cancelled. |
order.refunded | This is triggered when an order has been refunded. |
order.deleted | This is triggered when an order has been deleted. |
order.products.updated | This is triggered when an order products have been updated. |
order.payment.updated | This is triggered when an order payment has been updated. |
order.coupon.updated | This is triggered when an order coupon has been updated. |
order.total.price.updated | This is triggered when an order total price has been updated. |
order.shipment.creating | This is triggered when an order shipment is being created. |
order.shipment.created | This is triggered when an order shipment return has been created. |
order.shipment.cancelled | This is triggered when an order shipment return has been cancelled. |
order.shipment.return.creating | This is triggered when an order shipment return is being created. |
order.shipment.return.created | This is triggered when an order shipment return has been created. |
order.shipment.return.cancelled | This is triggered when an order shipment return has been cancelled. |
order.shipping.address.updated | This is triggered when an order shipment shipping address has been updated. |
Product
| Name | Description |
|---|---|
product.created | This event is triggered when a product has been created. |
product.updated | |
product.deleted | This event is triggered when a product has been deleted. |
product.available | |
product.quantity.low | This event is triggered when a product's stock is of low quantity. |
product.price.updated | This event is triggered when a product price has been updated. |
product.status.updated | This event is triggered when a product status has been changed. |
product.image.updated | This event is triggered when a product image has been updated. |
product.category.updated | This event is triggered when a product category has been updated. |
product.brand.updated | This event is triggered when a product brand has been updated. |
product.tags.updated | This event is triggered when a product tags have been updated. |
Shipping Companies
| Name | Description |
|---|---|
shipping.zone.created | This is triggered when a shipping zone has been created for a custom shipping company. |
shipping.zone.updated | This is triggered when a shipping zone has been updated for a custom shipping company. |
shipping.company.created | This is triggered when a custom shipping company has been created. |
shipping.company.updated | This is triggered when a custom shipping company has been updated. |
shipping.company.deleted | This is triggered when a custom shipping company has been deleted. |
Shipments
| Name | Description |
|---|---|
shipment.creating | This is triggered when a shipment is assigned to a shipping company. |
shipment.created | This is triggered when shipment is updated by the shipping company for the first time. |
shipment.cancelled | This is triggered when a shipment is cancelled. |
shipment.updated | This is triggered when a shipment is updated after creation. |
Customer
| Name | Description |
|---|---|
customer.created | This event is triggered when a customer has been created. |
customer.updated | This event is triggered when a customer has been updated. |
customer.login | This event is triggered when a customer has logged in to their account. |
customer.otp.request | This event is triggered when a customer's One-Time Password has been requested. |
Category
| Name | Description |
|---|---|
category.created | This event is triggered when a category has been created. |
category.updated | This event is triggered when a category has been updated. |
Brand
| Name | Description |
|---|---|
brand.created | This event is triggered when a brand has been created. |
brand.updated | This event is triggered when a brand has been updated. |
brand.deleted | This event is triggered when a brand has been deleted. |
Store
| Name | Description |
|---|---|
store.branch.created | This event is triggered when a store branch has been created. |
store.branch.updated | This event is triggered when a store branch has been updated. |
store.branch.setDefault | This event is triggered when a store branch has been set to be the default branch. |
store.branch.activated | This event is triggered when a store branch has been activated. |
store.branch.deleted | This event is triggered when a store branch has been deleted. |
storetax.created | This event is triggered when a store tax has been created. |
Cart
| Name | Description |
|---|---|
abandoned.cart | This event is triggered when an abandoned cart has been created. |
coupon.applied | This event is triggered when a coupon has been applied. |
Invoice
| Name | Description |
|---|---|
invoice.created | This event is triggered when the order status is either completed or restored. |
Special Offer
| Name | Description |
|---|---|
specialoffer.created | This event is triggered when a special offer has been created. |
specialoffer.updated | This event is triggered when a special offer has been updated. |
Miscellaneous
| Name | Description |
|---|---|
review.added | This event is triggered when a product's review has been added. |
Troubleshooting
Why Webhook Fails
The initial step in troubleshooting, regardless of the issue, would be to test for the situations.
Set Up Troubleshooting Environment
Part 1 | Set Up the Webhook Settings in Partners Portal
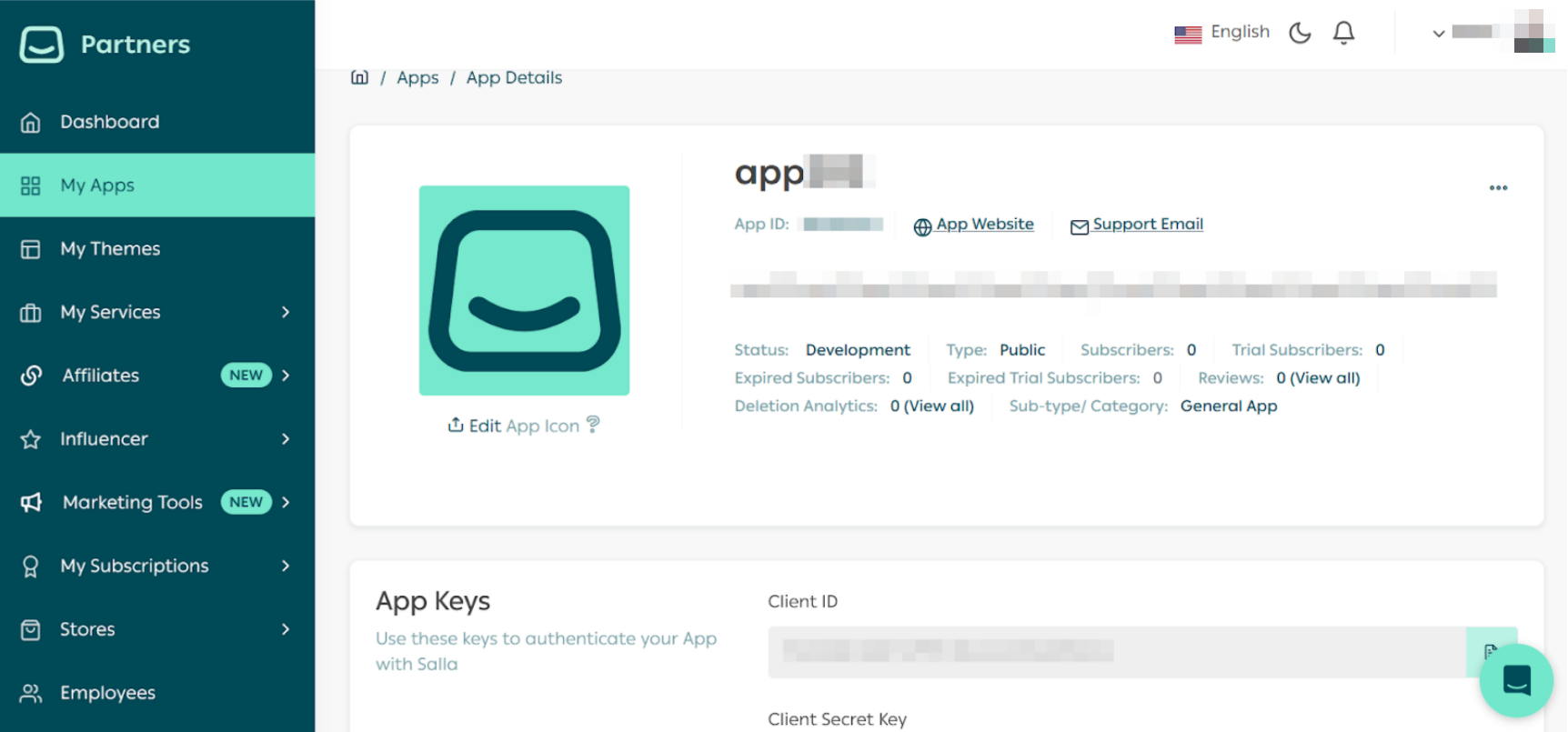
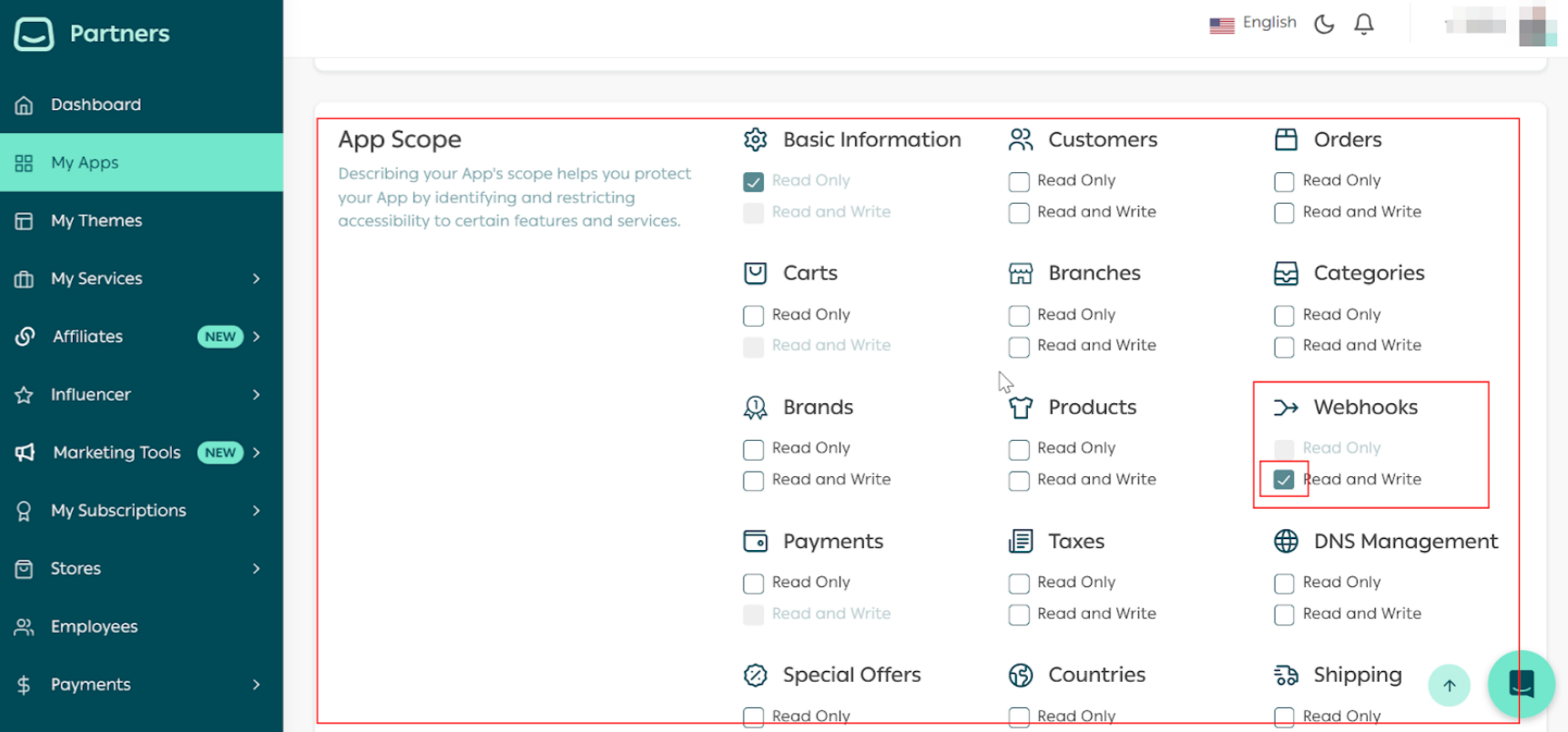
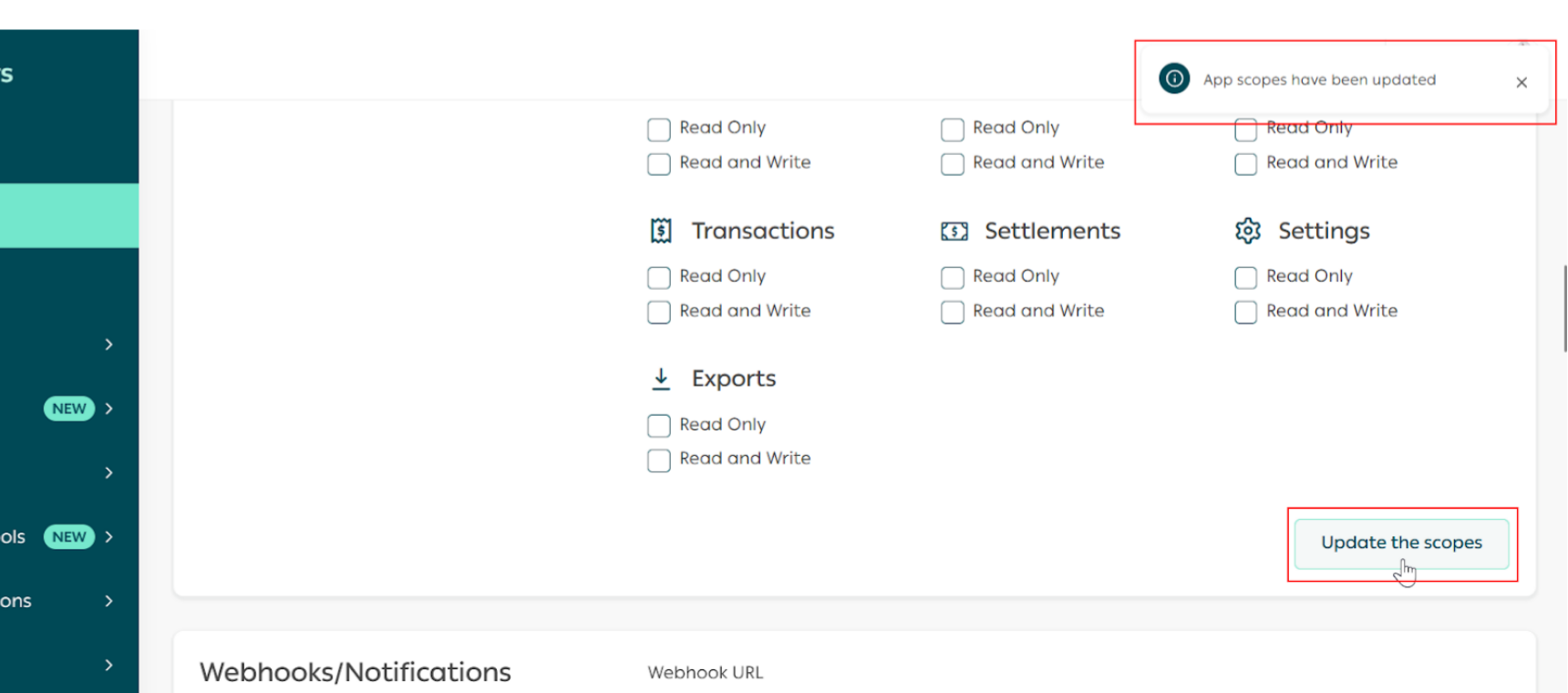
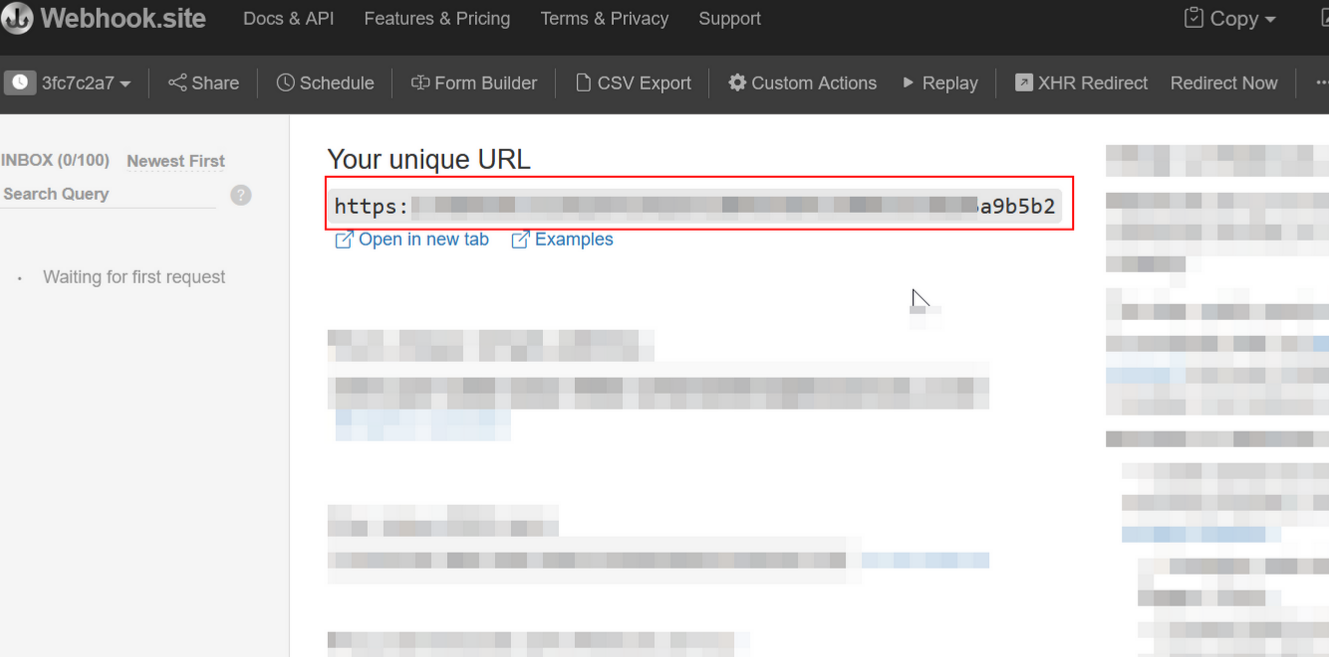
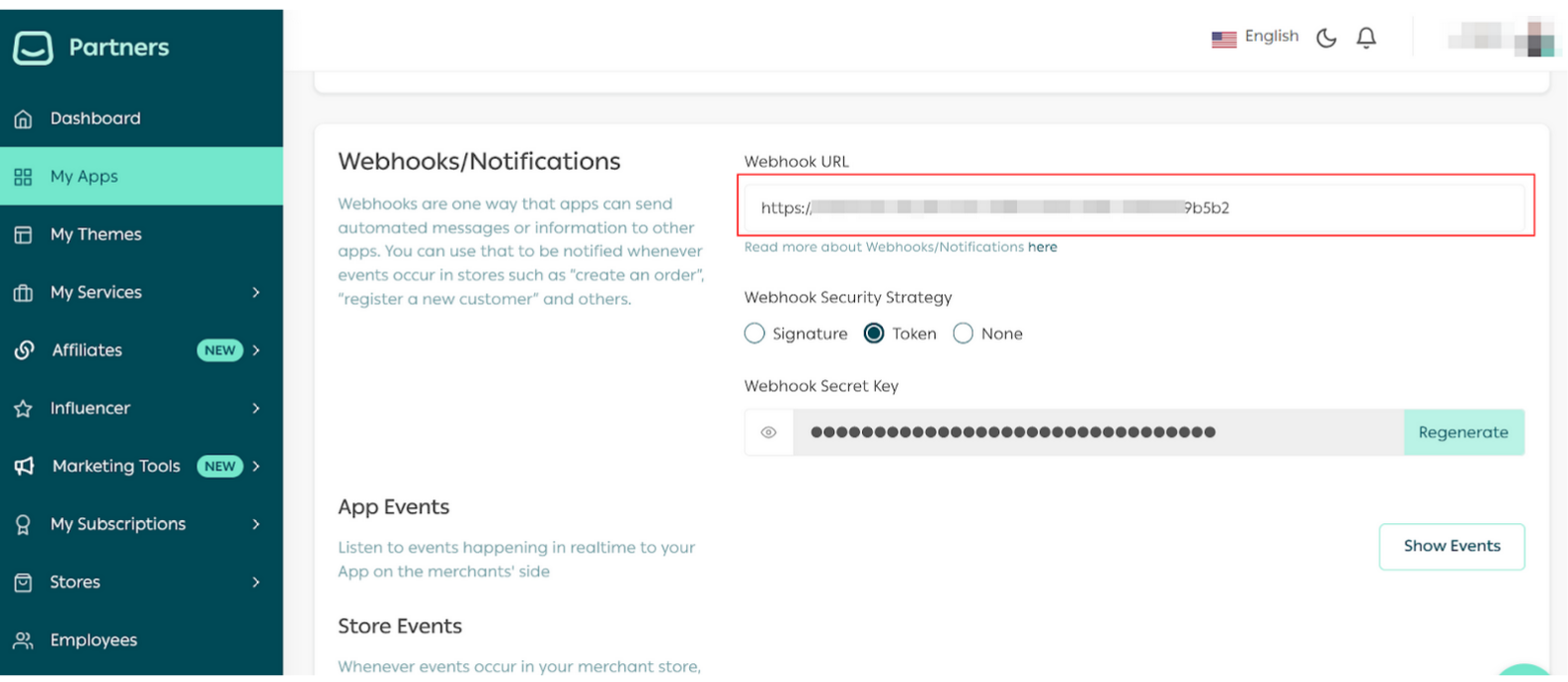
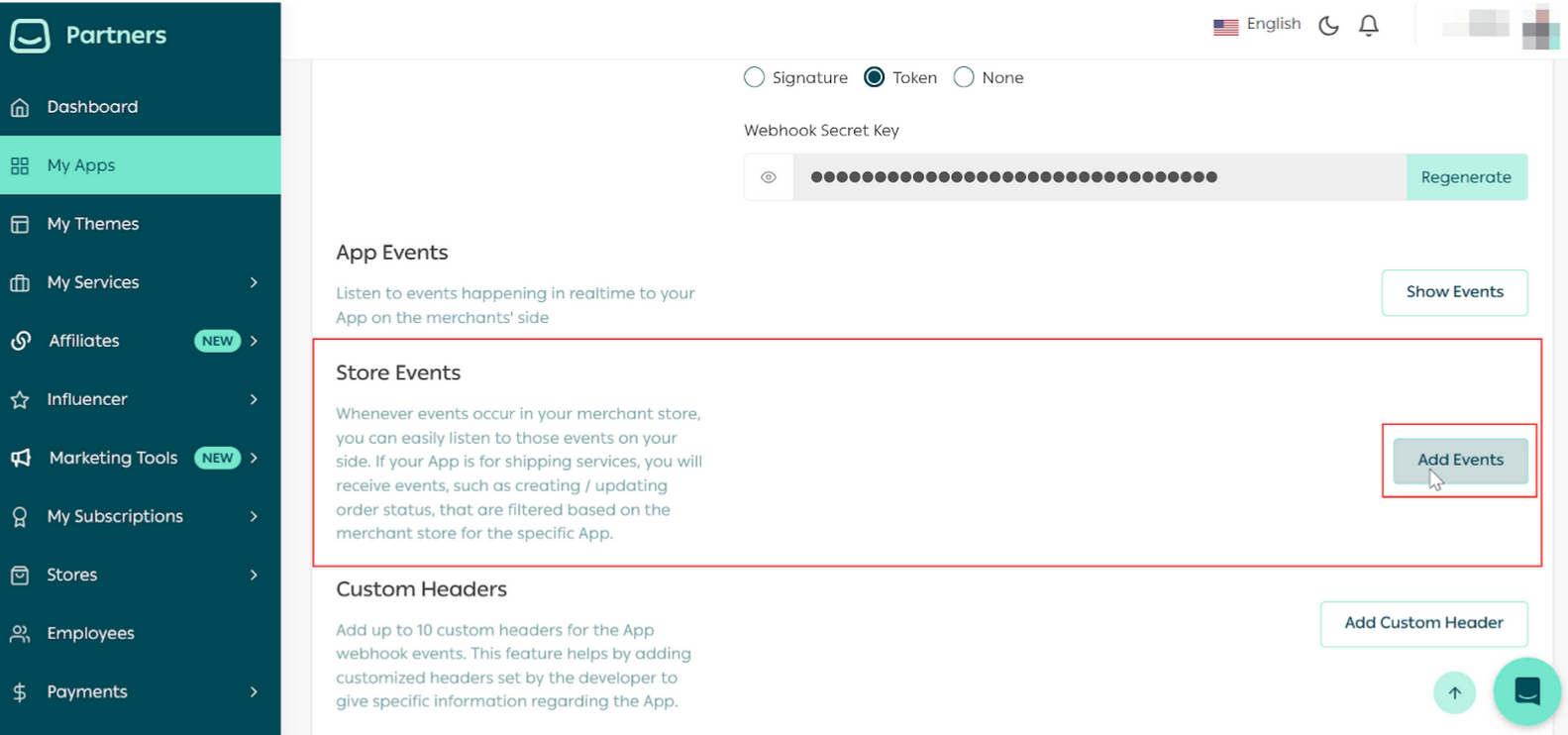
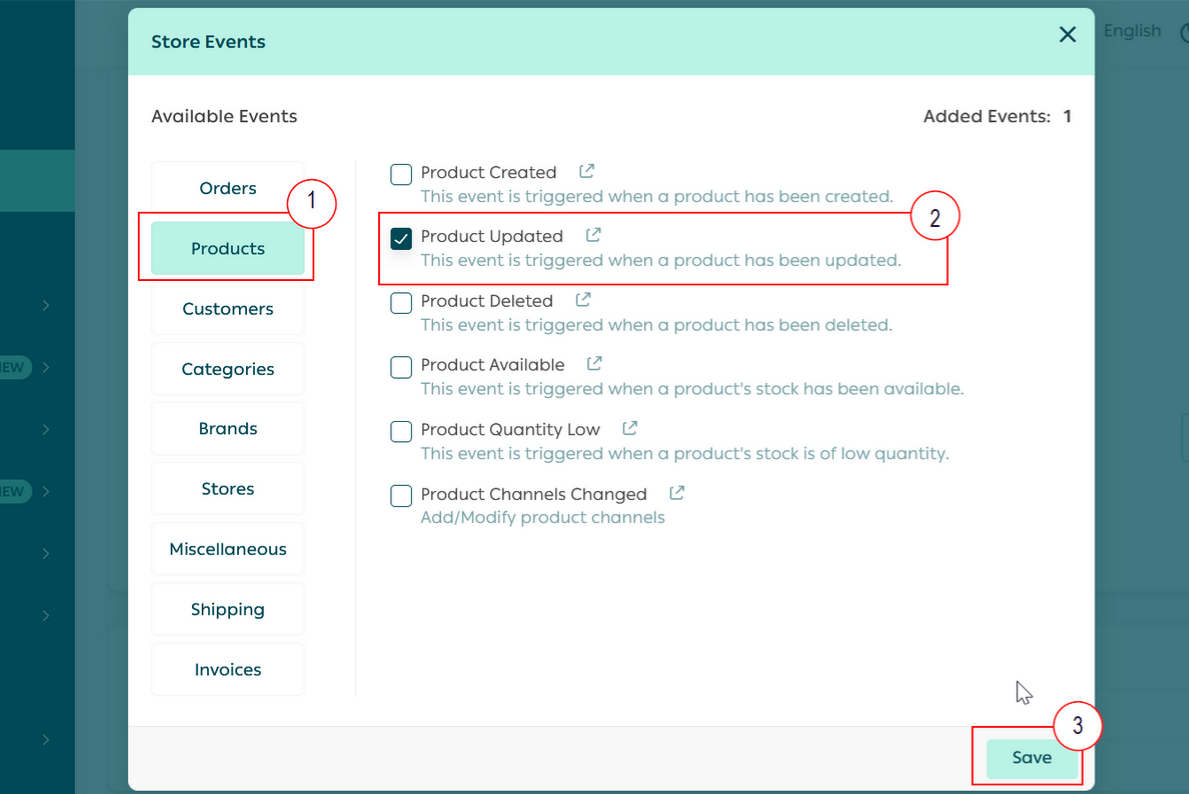
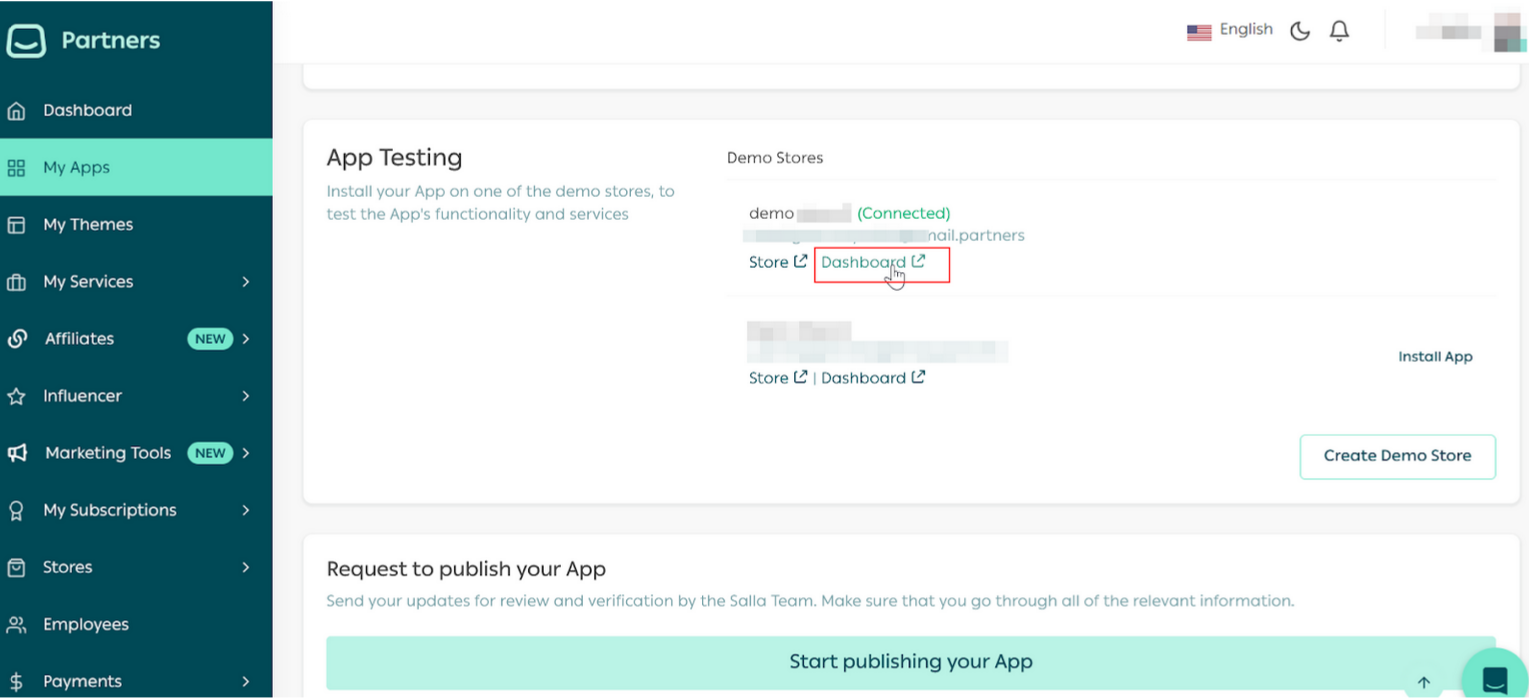
Part 2 | Install the App in the demo store
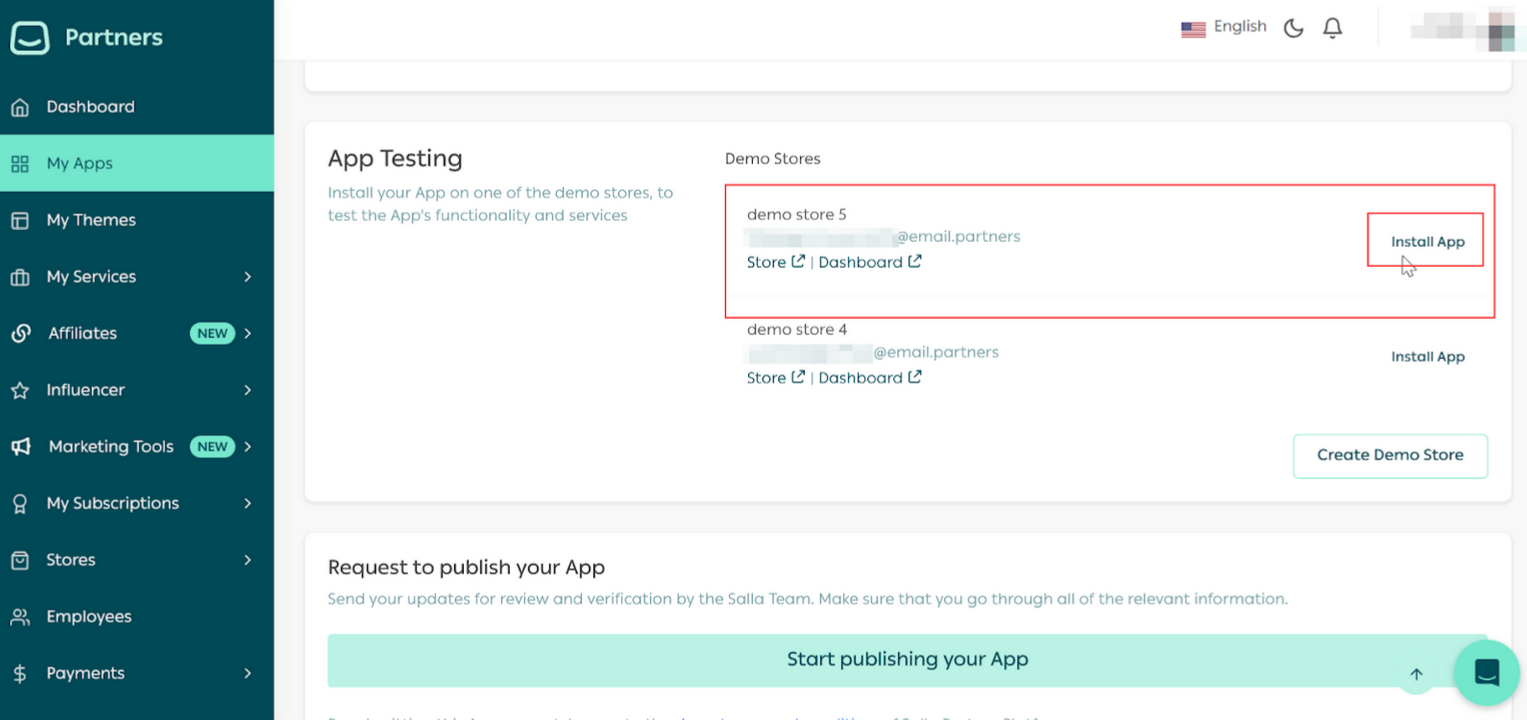
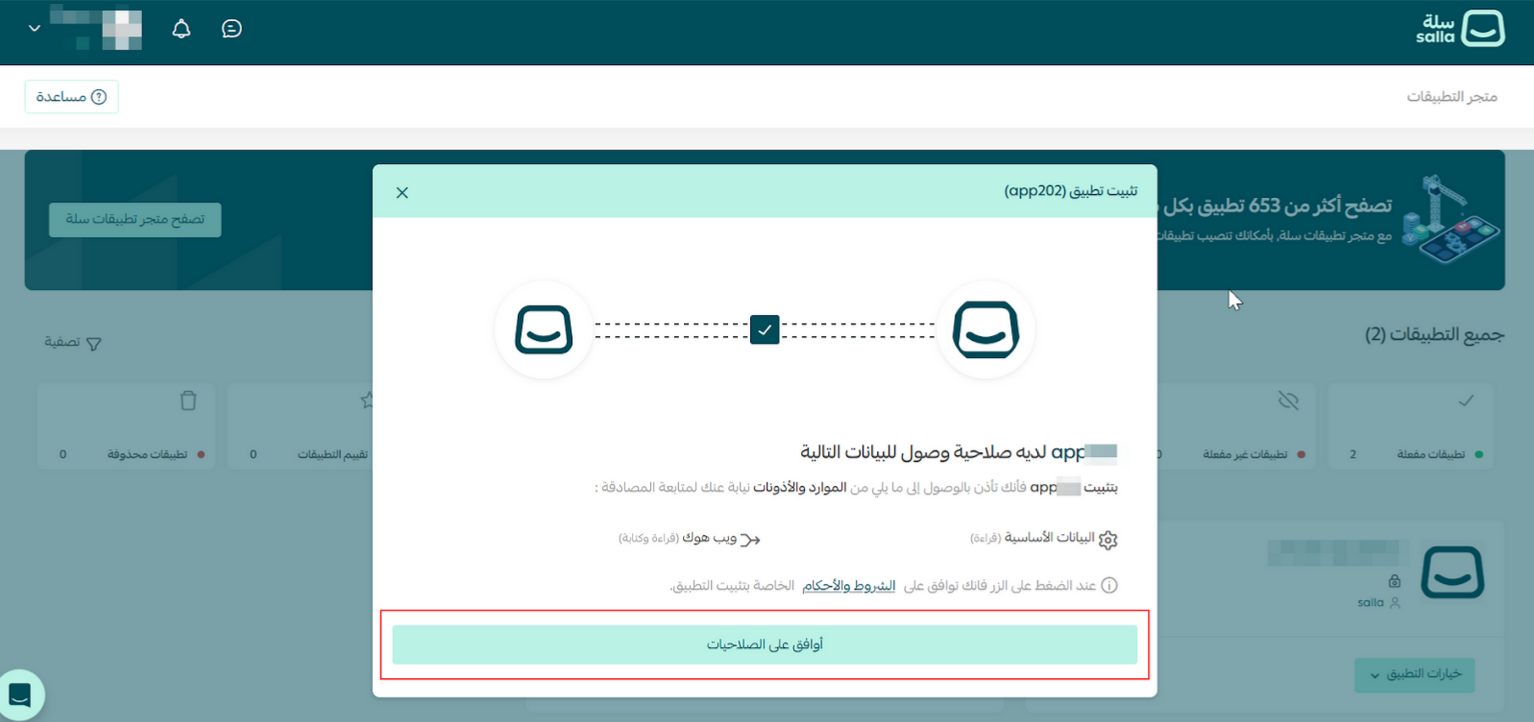
Note


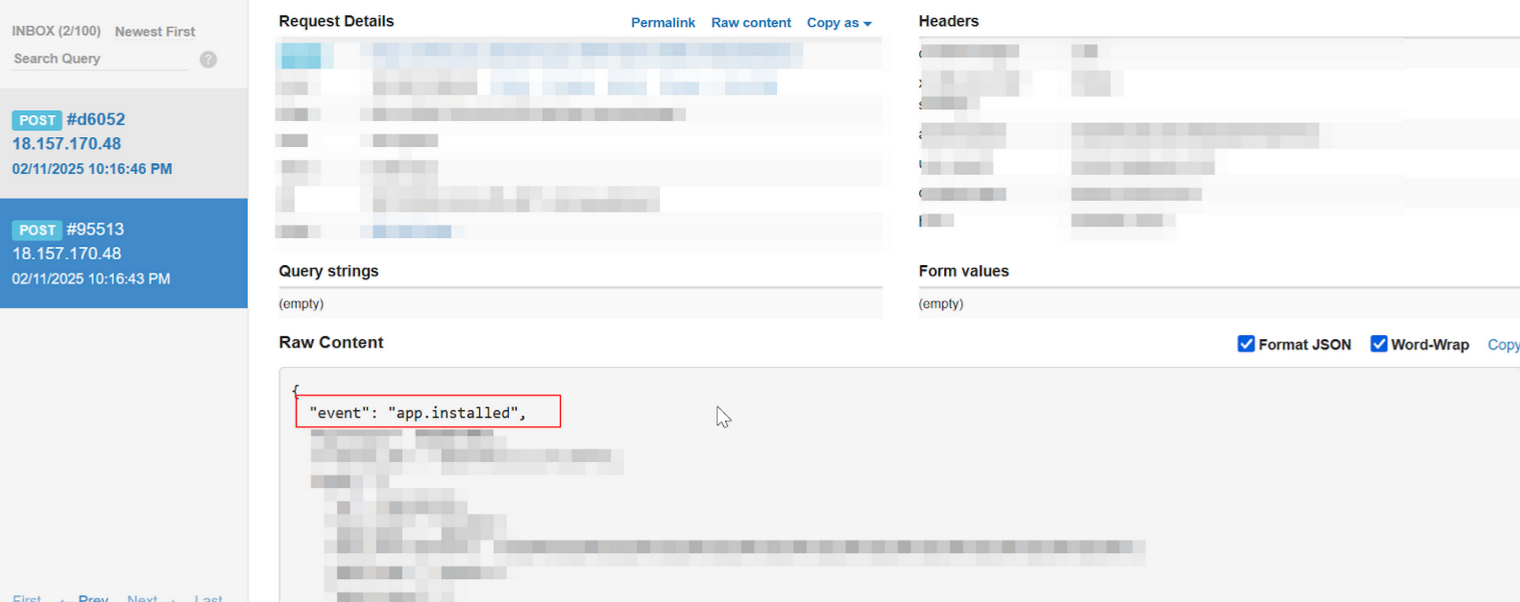
Part 3 | Test the Webhook using the Store dashboard
Note
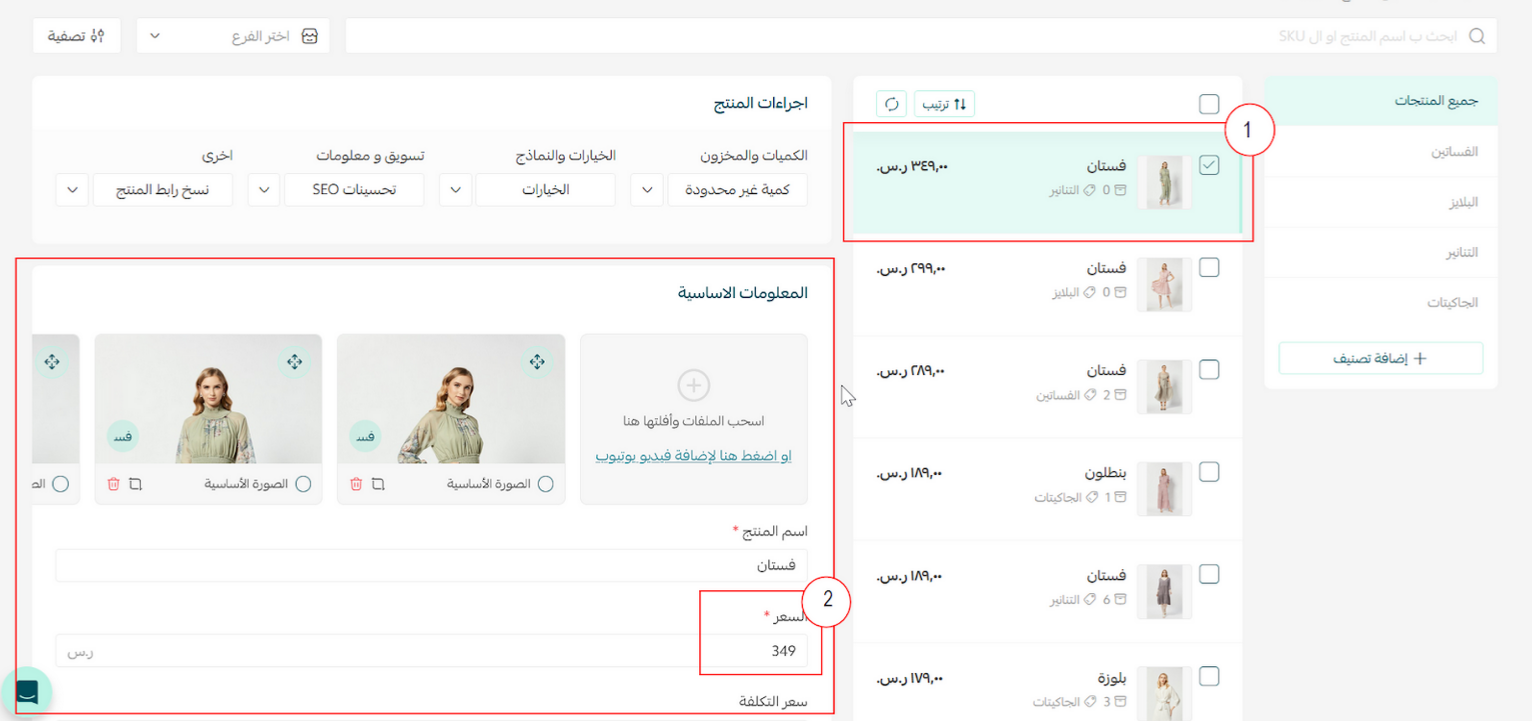
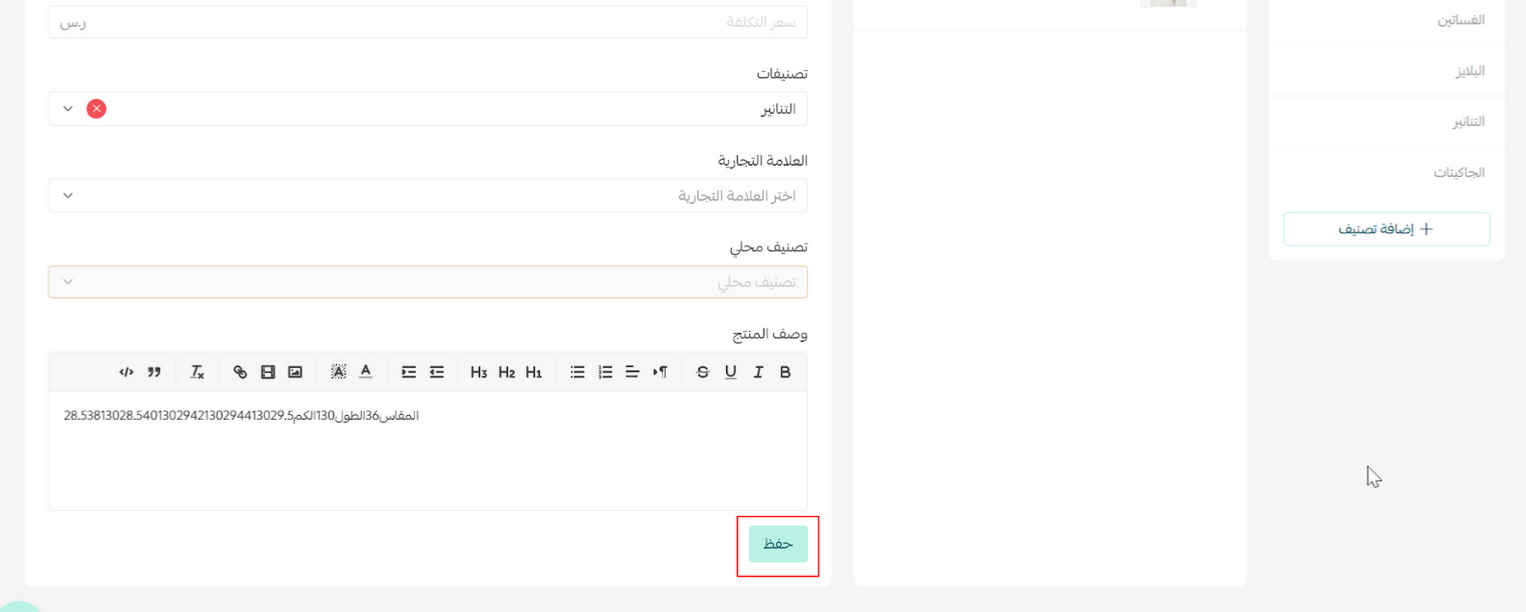
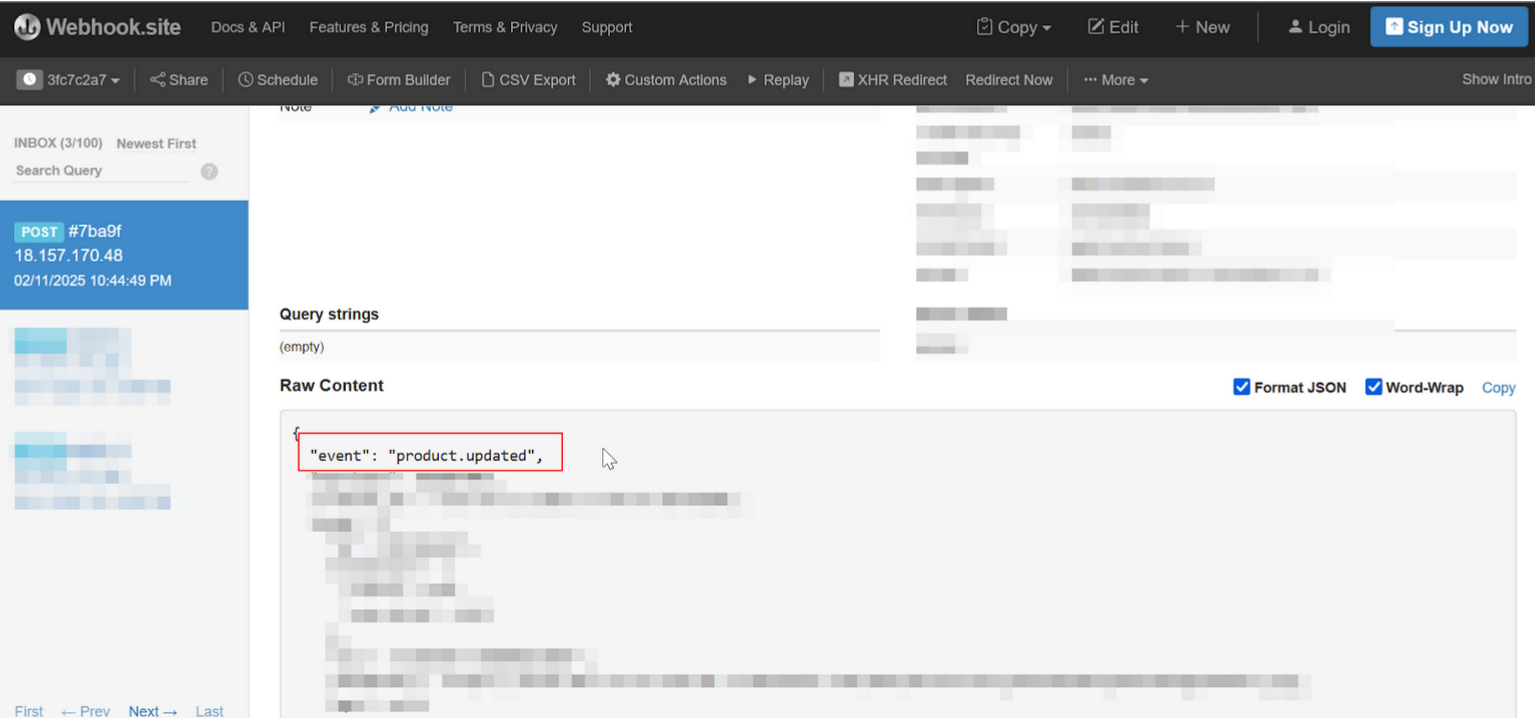
Part 4| Check Webhooks events with Salla Webhooks Log
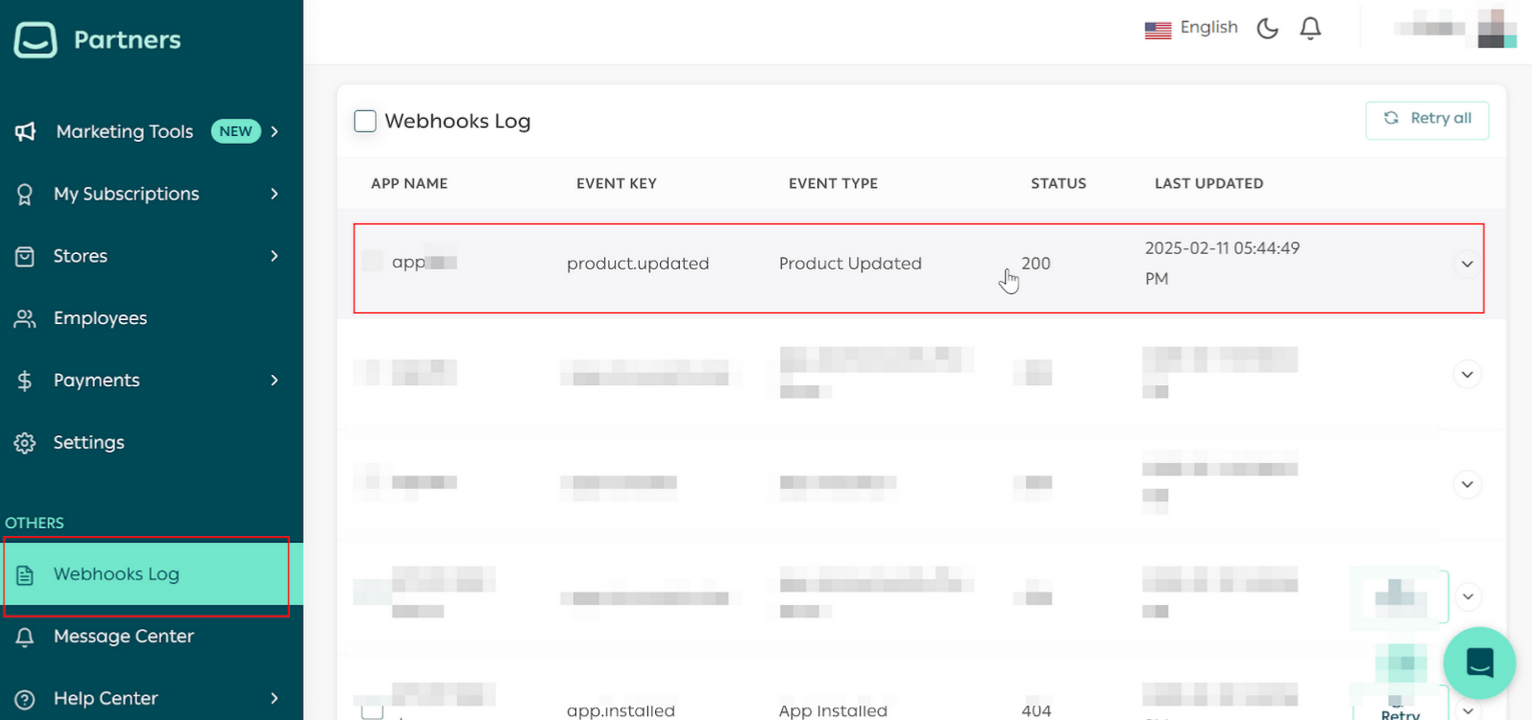
note
Check out the Salla Webhooks doc page for additional information.
🔍 Webhook Server Troubleshooting
POST data correctly.WARNING
🔍 URL Endpoint Access Troubleshooting
POST endpoint that, whenever a request is submitted to it, adds a timestamp to a log file.POST request over to SallaPOST call.🔍 POST Data Troubleshooting
POST request and save it to a file.order.created event:V2
V1
WebhookV2Response
Modified at 2025-12-15 09:54:37
